DISCONNECTED SPAMMER CASESTUDY
The Case of the Disconnected Spammer, 2004-01-18
On Jan 18th, our DNS root server measurements showed a sudden increase in traffic. It lasted for a little more than two days. Note in the graph below that about 12 hours after the initial spike, there is another increase. The second increase is mostly in MX, AAAA, and A6 records. The AAAA/A6 queries are for [a-m].root-servers.net, because those records timed out of the clients caches after not getting any responses for 12 hours.
The high number of MX queries should be a tip-off to what was going on here...
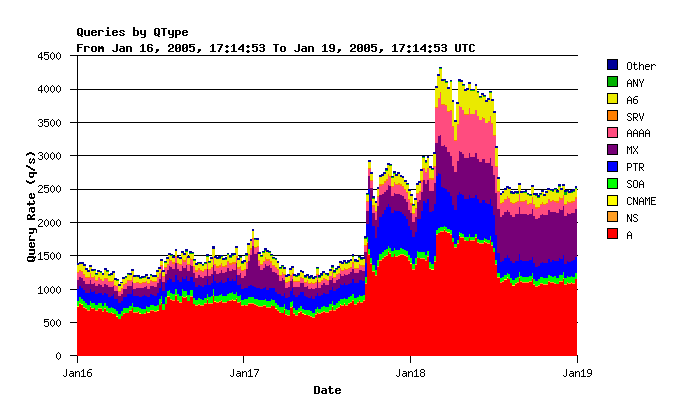
These graphs show that a single /24 network is responsible for a significant amount of the traffic. About 1700 queries/second averaged over the first 17 hours of Jan 19th! Or 35% of all queries received during that period.
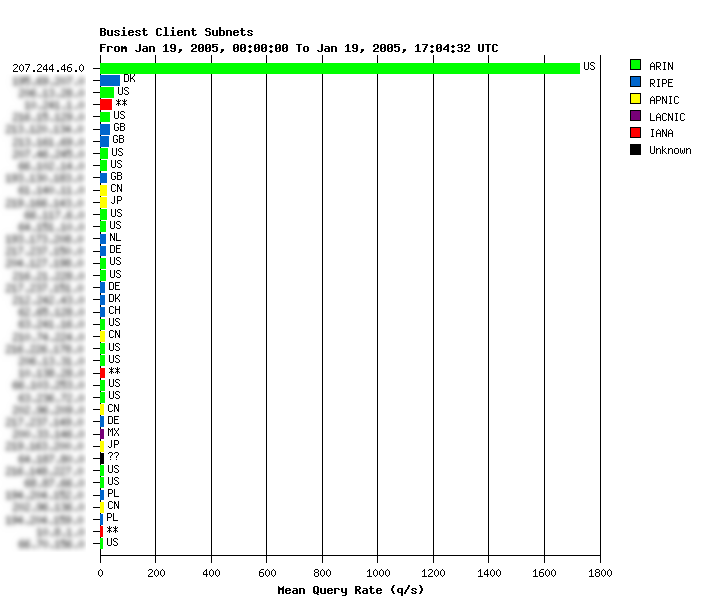
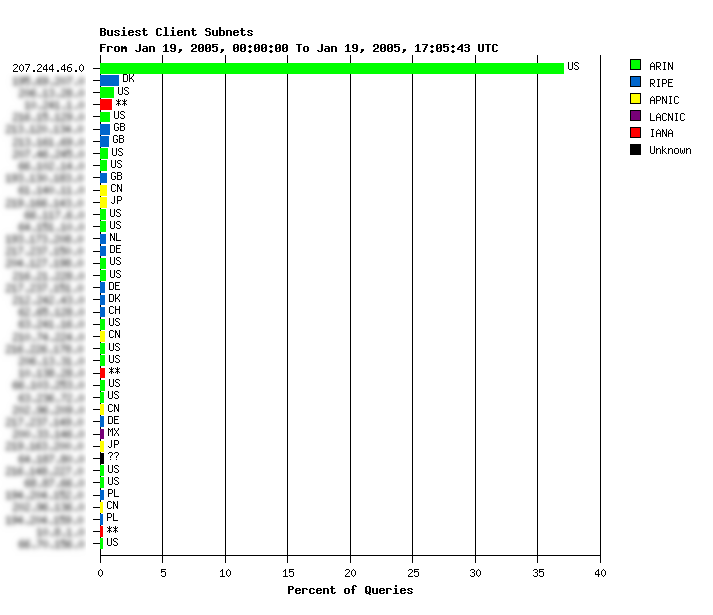
This is a much higher rate than we normally see from abusive sources. I wonder how many different hosts are involved?
> tcpdump -n -i em0 -c 100000 src net 207.244.46 | awk '{print $2}' | sort | uniq
207.244.46.21.1024
207.244.46.22.1024
207.244.46.23.1024
207.244.46.24.1024
207.244.46.25.1024
207.244.46.26.1024
207.244.46.28.1024
207.244.46.29.1024
207.244.46.30.1024
207.244.46.31.1024
207.244.46.33.1024
207.244.46.34.1024
207.244.46.35.1024
207.244.46.37.1024
207.244.46.38.1024
207.244.46.39.1024
207.244.46.40.1024
207.244.46.41.1024
207.244.46.42.1024
207.244.46.43.1024
207.244.46.44.1024
207.244.46.45.1024
207.244.46.46.1024
207.244.46.48.1024
207.244.46.49.1024
207.244.46.50.1024
207.244.46.51.1024
207.244.46.52.1024
207.244.46.53.1024
207.244.46.54.1024
207.244.46.55.1024
207.244.46.56.1024
207.244.46.57.1024
207.244.46.58.1024
207.244.46.59.1024
207.244.46.61.1024
207.244.46.62.1024
207.244.46.64.1024
207.244.46.65.1024
207.244.46.66.1024
207.244.46.67.1024
207.244.46.68.1024
207.244.46.69.1024
207.244.46.70.1024
207.244.46.72.4692
207.244.46.73.2137
207.244.46.74.2657
207.244.46.75.2593
207.244.46.76.3419
207.244.46.77.1796
207.244.46.78.2745
207.244.46.79.2427
207.244.46.80.2407
207.244.46.81.1338
207.244.46.82.1913
207.244.46.83.3891
207.244.46.84.2421
207.244.46.85.1972
207.244.46.86.2445
207.244.46.87.3626
207.244.46.88.1092
207.244.46.89.1507
207.244.46.90.4715
207.244.46.91.4978
207.244.46.92.3125
207.244.46.93.2774
207.244.46.94.2623
207.244.46.95.2380
207.244.46.96.3252
207.244.46.97.3466
207.244.46.98.2126
207.244.46.99.4252
207.244.46.100.1150
207.244.46.101.3849
207.244.46.102.4498
207.244.46.103.4887
207.244.46.104.3402
207.244.46.105.1177
207.244.46.106.4493
207.244.46.107.4185
207.244.46.108.4122
207.244.46.109.3093
207.244.46.110.3349
207.244.46.111.3668
207.244.46.112.3643
207.244.46.113.2588
207.244.46.114.3565
207.244.46.115.4164
207.244.46.116.2112
207.244.46.117.3984
Wow!
I wonder if they have reverse DNS set up correctly?
> host 207.244.46.21 21.46.244.207.IN-ADDR.ARPA domain name pointer 207-244-46-21.no-icmp-accepted.adsl.atl.ga.cdc.net > host 207.244.46.22 22.46.244.207.IN-ADDR.ARPA domain name pointer 207-244-46-22.no-icmp-accepted.adsl.atl.ga.cdc.net > host 207.244.46.23 23.46.244.207.IN-ADDR.ARPA domain name pointer 207-244-46-23.no-icmp-accepted.adsl.atl.ga.cdc.net > host 207.244.46.24 24.46.244.207.IN-ADDR.ARPA domain name pointer 207-244-46-24.no-icmp-accepted.adsl.atl.ga.cdc.net > host 207.244.46.25 25.46.244.207.IN-ADDR.ARPA domain name pointer 207-244-46-25.no-icmp-accepted.adsl.atl.ga.cdc.net
Okay...
Let's see who this network belongs to:
> whois -a 207.244.46.0
Chattanooga Data Connection, Inc. CHATDATA (NET-207-244-0-0-1)
207.244.0.0 - 207.244.63.255
Success Marketing Associates, LLC CDC-LEASED-IAG-40 (NET-207-244-40-0-1)
207.244.40.0 - 207.244.47.255
Success Marketing, you say?
> whois -a NET-207-244-40-0-1 OrgName: Success Marketing Associates, LLC OrgID: SMAL-3 Address: 701 N. Green Valley Parkway Address: Suite 200 City: Henderson StateProv: NV PostalCode: 89074 Country: US NetRange: 207.244.40.0 - 207.244.47.255 CIDR: 207.244.40.0/21 NetName: CDC-LEASED-IAG-40 NetHandle: NET-207-244-40-0-1 Parent: NET-207-244-0-0-1 NetType: Reassigned Comment: RegDate: 2005-01-10 Updated: 2005-01-10 OrgTechHandle: IPMAN10-ARIN OrgTechName: IP Manager OrgTechPhone: +1-800-477-1477 OrgTechEmail: ipmanager@successmarketingassoc.com
Hm, a network recently registered with ARIN? We sent a friendly email to ipmanager@successmarketingassoc.com. After a short wait, here is the reply:
Hi. This is the qmail-send program at mail.smsonline.net. I'm afraid I wasn't able to deliver your message to the following addresses. This is a permanent error; I've given up. Sorry it didn't work out. <ipmanager@successmarketingassoc.com>: This address no longer accepts mail.
You're not the only one who's sorry...
Let's try their ISP:
> whois -a NET-207-244-0-0-1 OrgName: Chattanooga Data Connection, Inc. OrgID: CHAT Address: PO Box 5269, 2003 Amnicola Hwy. City: Chattanooga StateProv: TN PostalCode: 37406 Country: US NetRange: 207.244.0.0 - 207.244.63.255 CIDR: 207.244.0.0/18 NetName: CHATDATA NetHandle: NET-207-244-0-0-1 Parent: NET-207-0-0-0-0 NetType: Direct Allocation NameServer: DNS1.CHATTANOOGA.CDC.NET NameServer: DNS2.CHATTANOOGA.CDC.NET Comment: ADDRESSES WITHIN THIS BLOCK ARE NON-PORTABLE RegDate: 1996-11-06 Updated: 2002-02-08 TechHandle: CNO2-ARIN TechName: Network Operations Center TechPhone: +1-423-266-3369 TechEmail: noc@cdc.net
We phoned 423-266-3369. An automated system gives us three choices: one for tech support, two for accounting information, three for sales. Tech support should be able to help.
Sadly, no. The woman we spoke with insisted that I call back and speak with someone in sales, because they are "in the other building." I am not making this up!
Maybe noc@cdc.net goes to a more clueful person than the one who answers tech support calls. We sent another message to noc@cdc.net. I didn't bounce, but we haven't received a reply yet. Probably shouldn't be surprised since they can't even run a web site.
At this point we wondered if Chattanooga Data Connection was indeed the ISP for Success Marketing Associates, LLC (or whoever is sourcing these packets). A traceroute reveals:
# traceroute -n 207.244.46.83 traceroute to 207.244.46.83 (207.244.46.83), 64 hops max, 40 byte packets 1 * * * 2 * * * 3 * * * 4 * * * ^C
Wow, so our first-hop router doesn't have a route for this network?
route-views.oregon-ix.net>show ip route 207.244.46.0 % Network not in table
I see.... I wonder where this traffic is really coming from?
Seems like either this IP space was hijacked, or someone was using it before, and then it broke. We decided to download a bunch of the archived BGP tables from routeviews and find out if anyone was recently advertising this space. The results:
2005-01-01-0000:* 207.244.46.0 64.200.151.12 0 7911 6389 6387 25817 21529 i 2005-01-02-0000:* 207.244.46.0 129.250.0.85 11 0 2914 209 25817 25817 25817 21529 i 2005-01-03-0000:* 207.244.46.0 129.250.0.85 11 0 2914 209 25817 25817 25817 21529 i 2005-01-04-0000:* 207.244.46.0 209.10.12.28 3 0 4513 701 6389 6387 25817 21529 i 2005-01-05-0000:* 207.244.46.0 209.10.12.28 3 0 4513 701 6389 6387 25817 21529 i 2005-01-06-0000:* 207.244.46.0 209.10.12.28 3 0 4513 701 6389 6387 25817 21529 i 2005-01-07-0000:* 207.244.46.0 216.218.252.152 0 6939 6389 6387 25817 21529 i 2005-01-08-0000: 2005-01-09-0000: 2005-01-10-0000: 2005-01-11-0000: 2005-01-12-0000:* 207.244.46.0/23 203.62.252.26 0 1221 4637 6461 30092 i 2005-01-13-0000:* 207.244.46.0/23 208.186.154.35 0 0 5650 6461 30092 i 2005-01-14-0000:* 207.244.46.0/23 208.186.154.35 0 0 5650 6461 30092 i 2005-01-15-0000:* 207.244.46.0/23 217.75.96.60 0 0 16150 15703 20495 6461 30092 i 2005-01-16-0000:* 207.244.46.0/23 129.250.0.11 6 0 2914 6461 30092 i 2005-01-17-0000:* 207.244.46.0/23 217.75.96.60 0 0 16150 15703 20495 6461 30092 i 2005-01-18-0000:* 207.244.46.0/23 196.7.106.245 0 0 2905 701 6461 30092 i 2005-01-19-0000"
AS 21529 is the aforementioned, clue-deprived CDC.net. Interesting that the space was more recently advertised by AS 30092, which turns out to be assertive.ca.
I wrote to the NOC at assertive.ca and received a quick and friendly reply from Chris Phillips. Turns out this space was announced by them on behalf of a new customer that turned out to be a spammer. Although the route was withdrawn, apparently their boxes remained connected. Assertive Networks disconnected their servers a short while later, and the flood of queries stopped.
Todays Internet Lesson: Don't just withdraw routes to spammers, yank the network cables out of their boxes!
